Decoding Government Spyware Alerts on Your Mobile Device
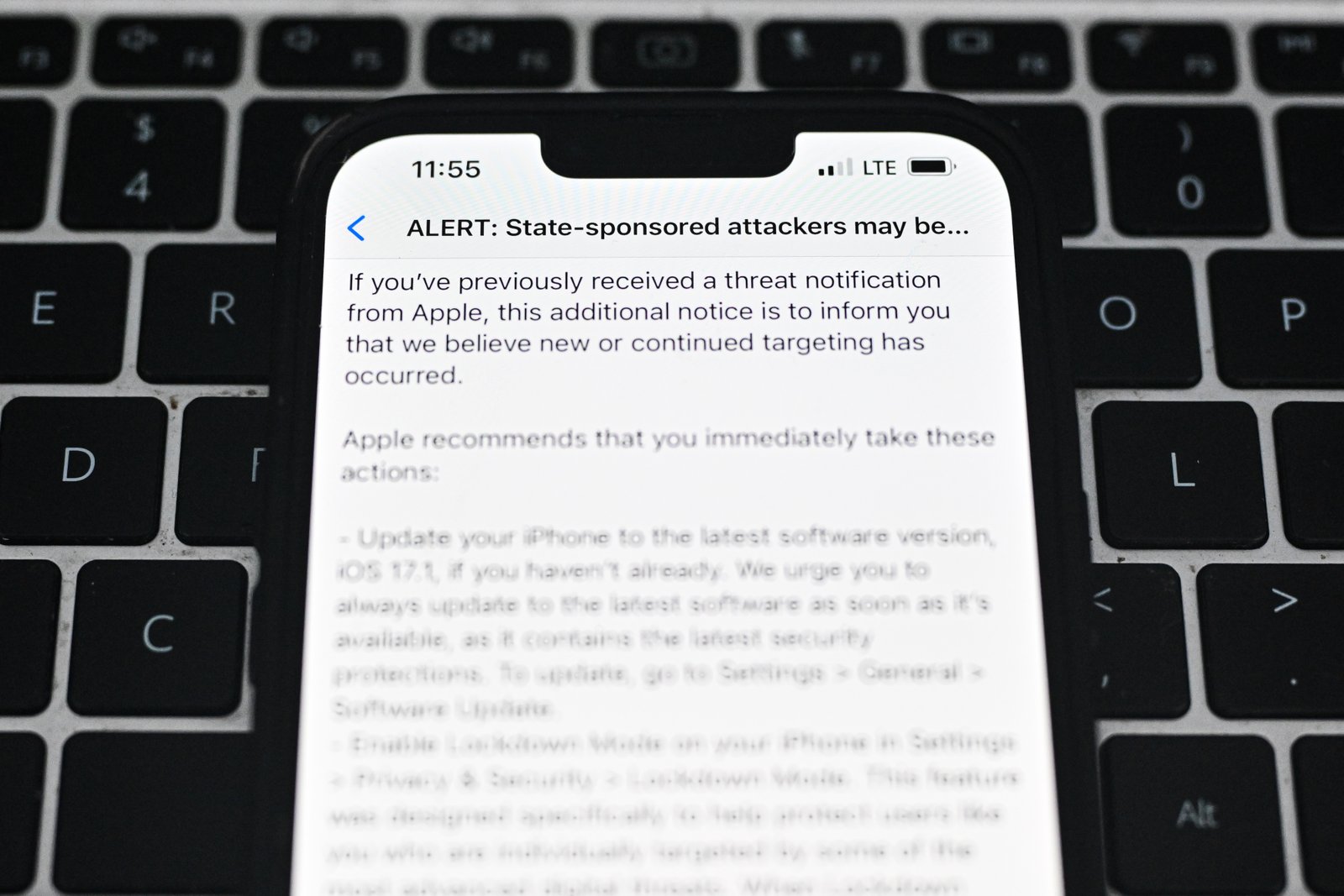
picture this: your smartphone suddenly displays a notification stating, “Your device was targeted by government-grade spyware.” Such warnings are becoming more frequent as major technology companies like Apple, Google, and WhatsApp intensify their efforts to alert users about elegant cyber threats involving advanced spyware.
The Escalation of Spyware Alert incidents
The frequency of individuals receiving alerts about attempted or prosperous spyware intrusions has grown significantly in recent years. These warnings often relate to attacks orchestrated by state-backed actors deploying surveillance tools created by firms such as NSO Group, intellexa, and Paragon Solutions. Even though these companies claim their software is intended for lawful monitoring,numerous investigations have linked their products to abuses targeting journalists,activists,politicians,and corporate executives worldwide.
It is indeed critically important to note that receiving such an alert does not necessarily confirm that your device was compromised.In many instances-especially with platforms like Apple and WhatsApp-the intrusion attempt may have been blocked before any data breach occurred.
Essential Actions Upon Receiving a Spyware Notification
- Take the warning seriously: These alerts are generated through sophisticated telemetry systems refined over years of cybersecurity research; false positives are uncommon.
- Maintain composure: While it’s natural to feel alarmed-many cybersecurity experts report initial shock upon seeing these messages-calmly following recommended steps is crucial.
- Keeps your software up-to-date: Regularly update your operating system and applications as many security patches address vulnerabilities exploited by spyware campaigns.
- activate advanced security measures:
- If you use Apple devices: Enable the Lockdown Mode, introduced in late 2022. This feature limits certain functionalities to reduce exposure against highly targeted exploits; it has successfully blocked multiple zero-day attacks since its launch.
- If you rely on Google services or Android devices: Join Google’s Advanced Protection Program, which enforces the use of physical security keys alongside othre stringent protections designed for high-risk users such as political figures or investigative reporters.
- Avoid clicking suspicious links or opening unknown attachments: Many infections begin with phishing attempts disguised as legitimate communications; vigilance here can prevent compromise entirely.
- Create frequent backups & reboot regularly:
- This habit helps clear temporary malware activity while preserving clean copies of essential data for recovery if needed later on.
Selecting Support Based on Your Professional Context
Your response after receiving a government spyware alert will vary depending on your role and environment. Different sectors require tailored approaches when addressing potential compromises caused by state-level surveillance tools. Below is guidance for various groups seeking assistance following such notifications:
Civil Society Actors: Journalists, Human Rights Defenders & Researchers
If you operate within vulnerable civil society domains-such as investigative journalism exposing corruption or human rights advocacy-you can access specialized support networks offering forensic analysis at no cost. Digital rights organizations provide confidential assistance using remote diagnostic utilities like the Mobile Verification Toolkit (MVT), empowering even non-technical users to detect signs of intrusion before escalating concerns further.
Larger Institutions & Political Organizations
If you belong to political parties or multinational corporations equipped with internal cybersecurity teams but lacking expertise in handling government-grade espionage threats, external consultation may be necessary. Private firms specializing in mobile device forensics offer extensive services ranging from app-based preliminary scans (e.g., iVerify) up through full forensic examinations conducted remotely or onsite (e.g., Safety Sync Group).
Bespoke Forensic Services & Expert Resources Available
- MVT Toolkit access: An open-source solution enabling moderately skilled users to scan smartphones for indicators consistent with Pegasus-like infections prior to seeking professional help;
- Pioneering Security Firms: The likes of Hexordia deliver customized investigations led by seasoned forensic analysts experienced in both governmental breaches and private-sector espionage cases;
- < b >TLPBLACK Team Expertise: A select elite group formerly part of Kaspersky’s GReAT unit offers direct channels for suspected victims requiring deep-dive analyses into complex attack methodologies;
- < b >Crowdsourced Intelligence Platforms: Mobile cybersecurity company Lookout operates reporting mechanisms where individuals can submit incidents possibly linked to state-sponsored malware infections – triggering dedicated threat research team involvement;





